UBoat is a proof-of-concept HTTP Botnet that designed to replicate a full weaponized commercial botnet.
That Uboat is coded in programming native c++ and c you can smoothly working well with your clients or target
and http botnet can have feature dashbaord that easy to control and managed easily.
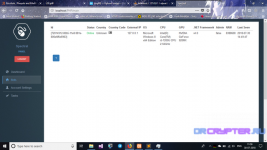
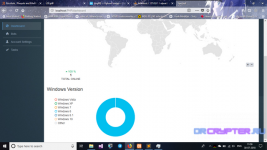
That Uboat is coded in programming native c++ and c you can smoothly working well with your clients or target
and http botnet can have feature dashbaord that easy to control and managed easily.
The main objective behind creating this offensive project was to aid security researchers and to enhance the understanding of commercial HTTP loader style botnets. We hope this project helps to contribute to the malware research community and people can develop efficient countermeasures.
Warning : Usage of UBoat without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.
Features
Written in C++ with no dependencies.
Encrypted C&C communications.
Persistence to prevent your control from being lost.
Connection redundancy (Uses a fallback server address or domain).
DDoS methods (TCP & UDP Flood).
Task Creation System (Altering system HWID, Country, IP, OS.System).
Remote command execution.
Update and uninstall other malware.
Download and execute other malware.
Active as well as a passive key-logger.
Enable Windows RDP.
Plugin system for easy feature updates.2
Warning : Usage of UBoat without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.
Features
Written in C++ with no dependencies.
Encrypted C&C communications.
Persistence to prevent your control from being lost.
Connection redundancy (Uses a fallback server address or domain).
DDoS methods (TCP & UDP Flood).
Task Creation System (Altering system HWID, Country, IP, OS.System).
Remote command execution.
Update and uninstall other malware.
Download and execute other malware.
Active as well as a passive key-logger.
Enable Windows RDP.
Plugin system for easy feature updates.2




